pavelmobile
Private
- Messages
- 59
Any developer very well knows how much time and effort is spent on independent development of an efficient algorithm and he has an unconditional right to defend it.
We're sure, that many users faced these common situations:
1. Decompiling *.ex4 files to investigate the logic of work and/or to intruduce modifications. With the latest build of the MT4 terminal, this process has become more complicated, but nevertheless specialists experienced in breaking successfully analyze the content and make unauthorized changes, including disabling trial protection and various bindings.
2. Trivial renaming of compiled files names, name of the manufacturer (#property copyright) for the purpose of issuing these files as different or "own" products.
We are developing a software solution that will help developer and their customers to protect their source code from unauthorized research, modification, renaming and resale.
This protection is implemented at the primary level of the source code by the dynamic encryption algorithms developed by us, without any additional libraries or external tools of protection from decompilation, i.e. the *.mq4 source code itself is changed.
Every experienced programmer can make sure by his own with the example above, that the subsequent compilation of the encrypted mq4 source code extremely complicates the process of studying and analyzing it, or makes it almost impossible. Also, anyone can test the protective encryption algorithm for free by sending any* source code in *.mq4 format to the email codeprotector@ypy.cc (see the details below)
Current features (beta version):
1. Dynamic Encryption of a source code with a unique proprietary algorithm
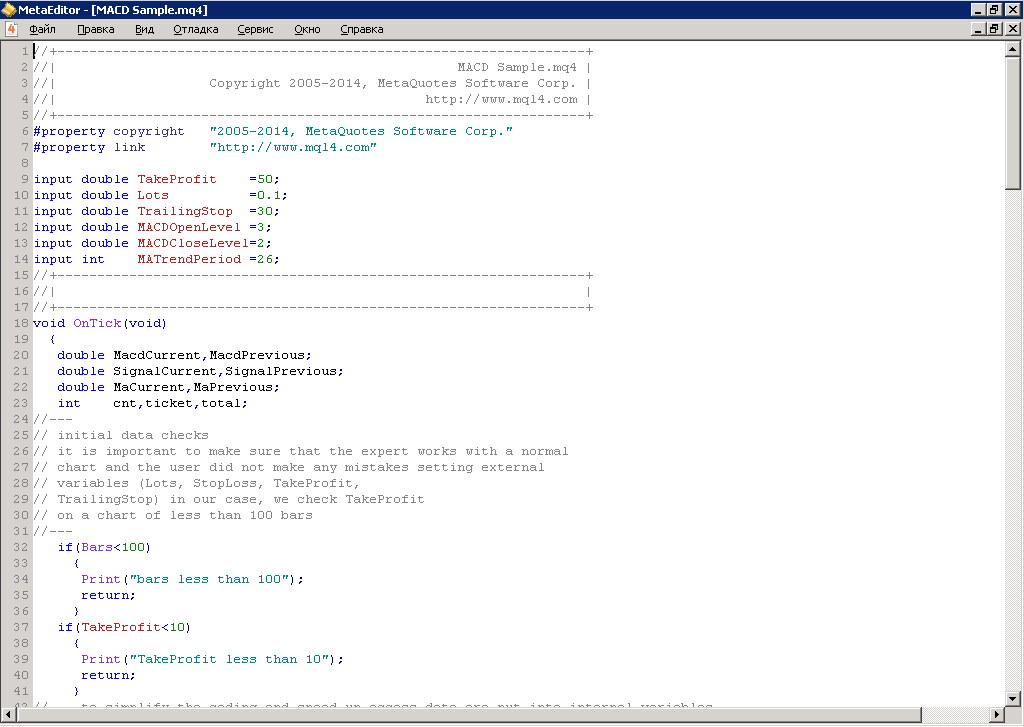
Example 1: This is the original source code before encryption (file attached)
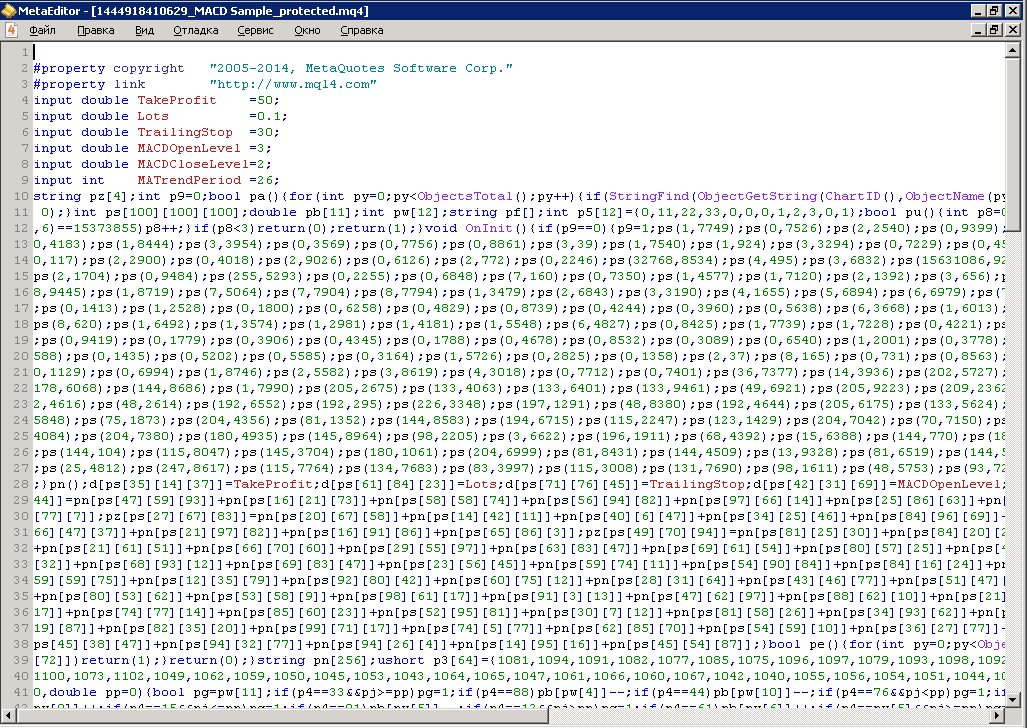
Example 2: This is the source code after the dynamic encryption (file attached)
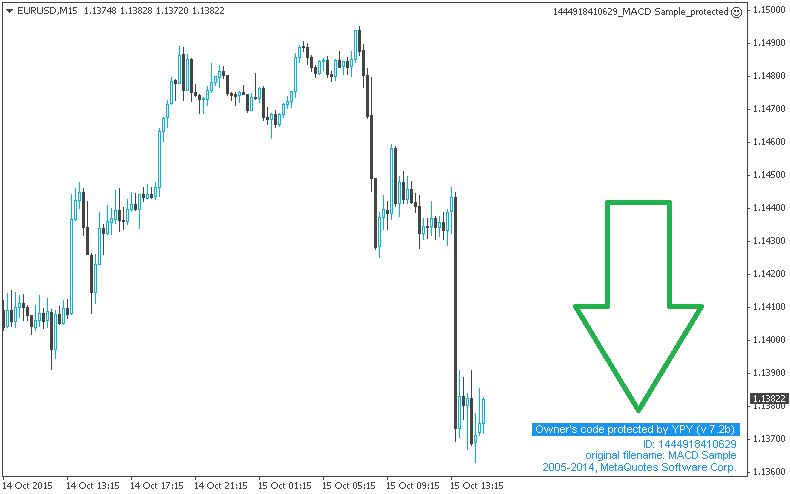
2. In order to further protect the owner of the code, complex protection information is automatically integrated into each encrypted source code (the info is shown on the graph in the lower right corner).
What is displayed:
+ Information containing the ID of encryption of the source code (with which the owner can always personalize a specific instance of the product). This can be very convenient for example, the owner of the code can understand which specific instance of the product was illegally published or has been cracked.
+ Original file name ("original filename"), which was used when the owner of the source code performed the encryption. Any subsequent change of the original protected file name will lead to a damage of logic (only addition to original names is permitted for convenience). Thus, it would be very difficult for attackers to completely change the file name.
+ Name of the manufacturer (#property copyright). At the time of encrypting this data is read from the source and is stored in encrypted form. Thus, even if attackers will make changes to the compiled *.mq4 file, changing this property to another manufacturer, then the graph will continue to report the manufacturer specified by the original owner.
Any subsequent unauthorized modification of the information displayed on the graph leads to a damage of logic.
Example 3: This is how the informational block looks like
Later, when we'll achieve a high percentage of compatibility with a variety of dynamic encryption codes, we plan to create a software product with a flexible and convenient built-in protected licensing system (limiting the time of usage, the account number, the name of the owner, to the trade server, etc.), which the user could use locally on his computer to protect his source, without transferring it to anyone.
Those developers who will actively cooperate with us by full and professional testing of our algorithm of the dynamic encryption will receive premium status of professional users with advanced features and extended limits of use.
It will be convenient and safe to share the source code into an encrypted form for developers who are constantly collaborating with customers by developing a variety of source codes.
Experience shows that even if you do not give the code to anyone and use it exclusively for your own needs on the VPS, it is much safer to use it in encrypted binded to your accounts.
How can you encrypt any* source code in the *.mq4 format?
At the moment it is being debugging and it is possible to make it by doing the following simple steps:
1. Send any email to the address codeprotector@ypy.cc
2. After receiving a reply with an activation code, respond to it (whith the activation code preserved in the answer)
3. Then you will receive an email confirming that you can send to this address any* source code in the *.mq4 format for protecting encryption.
4. You send *.mq4 files and after a while you get an email with already encrypted source code (the ID number and «_protected» words are added to the name of the source code, which can be easily removed).
All the files are processed automatically, we do not analyze or use the submitted files, except for their protective encryption, removing, debugging the technical compatibility of the encryption algorithm, initiated by the user in case if the encrypted source code contains errors or could not be encrypted. If you prefer not to send the source code by e-mail and/or just do not trust anyone, you can simply wait until we create a standalone software product for self-protection of the source code locally on your computer.
* Any *.mq4 source code being sent must not be previously encrypted and must be able to be compiled into *.ex4 without warnings and errors. You must first check it out yourself.
If the source code is encrypted with errors or is not encrypted, but it was fully functional before encryption (you should check this out before) and you are sure that you did not make any changes, please notify us and report the following:
1. ID number of encryption.
2. What exactly does not works or works incorrectly.
3. Describe in details how to reproduce the error, attach screenshots if possible.
P.S. Since we often receive various requests and suggestions, please keep in mind that we do not accept any orders for programming, as we perform software development for our own needs and development of the final products. There are many qualified third-party professionals who are ready to fulfill all your orders for the development of programs in the "Freelance" section of the Market. Also, we do not have and do not plan to have a software solution for decoding the source code back to the original form. All requests to send previously sent original source code, including persons representing their owners will be ignored. So please, do not ask us to do it.
!!!Anyone who understands the purpose of this software and who finds this useful is welcome to comment the post.
We're sure, that many users faced these common situations:
1. Decompiling *.ex4 files to investigate the logic of work and/or to intruduce modifications. With the latest build of the MT4 terminal, this process has become more complicated, but nevertheless specialists experienced in breaking successfully analyze the content and make unauthorized changes, including disabling trial protection and various bindings.
2. Trivial renaming of compiled files names, name of the manufacturer (#property copyright) for the purpose of issuing these files as different or "own" products.
We are developing a software solution that will help developer and their customers to protect their source code from unauthorized research, modification, renaming and resale.
This protection is implemented at the primary level of the source code by the dynamic encryption algorithms developed by us, without any additional libraries or external tools of protection from decompilation, i.e. the *.mq4 source code itself is changed.
Every experienced programmer can make sure by his own with the example above, that the subsequent compilation of the encrypted mq4 source code extremely complicates the process of studying and analyzing it, or makes it almost impossible. Also, anyone can test the protective encryption algorithm for free by sending any* source code in *.mq4 format to the email codeprotector@ypy.cc (see the details below)
Current features (beta version):
1. Dynamic Encryption of a source code with a unique proprietary algorithm
Example 1: This is the original source code before encryption (file attached)

Example 2: This is the source code after the dynamic encryption (file attached)

2. In order to further protect the owner of the code, complex protection information is automatically integrated into each encrypted source code (the info is shown on the graph in the lower right corner).
What is displayed:
+ Information containing the ID of encryption of the source code (with which the owner can always personalize a specific instance of the product). This can be very convenient for example, the owner of the code can understand which specific instance of the product was illegally published or has been cracked.
+ Original file name ("original filename"), which was used when the owner of the source code performed the encryption. Any subsequent change of the original protected file name will lead to a damage of logic (only addition to original names is permitted for convenience). Thus, it would be very difficult for attackers to completely change the file name.
+ Name of the manufacturer (#property copyright). At the time of encrypting this data is read from the source and is stored in encrypted form. Thus, even if attackers will make changes to the compiled *.mq4 file, changing this property to another manufacturer, then the graph will continue to report the manufacturer specified by the original owner.
Any subsequent unauthorized modification of the information displayed on the graph leads to a damage of logic.
Example 3: This is how the informational block looks like

Later, when we'll achieve a high percentage of compatibility with a variety of dynamic encryption codes, we plan to create a software product with a flexible and convenient built-in protected licensing system (limiting the time of usage, the account number, the name of the owner, to the trade server, etc.), which the user could use locally on his computer to protect his source, without transferring it to anyone.
Those developers who will actively cooperate with us by full and professional testing of our algorithm of the dynamic encryption will receive premium status of professional users with advanced features and extended limits of use.
It will be convenient and safe to share the source code into an encrypted form for developers who are constantly collaborating with customers by developing a variety of source codes.
Experience shows that even if you do not give the code to anyone and use it exclusively for your own needs on the VPS, it is much safer to use it in encrypted binded to your accounts.
How can you encrypt any* source code in the *.mq4 format?
At the moment it is being debugging and it is possible to make it by doing the following simple steps:
1. Send any email to the address codeprotector@ypy.cc
2. After receiving a reply with an activation code, respond to it (whith the activation code preserved in the answer)
3. Then you will receive an email confirming that you can send to this address any* source code in the *.mq4 format for protecting encryption.
4. You send *.mq4 files and after a while you get an email with already encrypted source code (the ID number and «_protected» words are added to the name of the source code, which can be easily removed).
All the files are processed automatically, we do not analyze or use the submitted files, except for their protective encryption, removing, debugging the technical compatibility of the encryption algorithm, initiated by the user in case if the encrypted source code contains errors or could not be encrypted. If you prefer not to send the source code by e-mail and/or just do not trust anyone, you can simply wait until we create a standalone software product for self-protection of the source code locally on your computer.
* Any *.mq4 source code being sent must not be previously encrypted and must be able to be compiled into *.ex4 without warnings and errors. You must first check it out yourself.
If the source code is encrypted with errors or is not encrypted, but it was fully functional before encryption (you should check this out before) and you are sure that you did not make any changes, please notify us and report the following:
1. ID number of encryption.
2. What exactly does not works or works incorrectly.
3. Describe in details how to reproduce the error, attach screenshots if possible.
P.S. Since we often receive various requests and suggestions, please keep in mind that we do not accept any orders for programming, as we perform software development for our own needs and development of the final products. There are many qualified third-party professionals who are ready to fulfill all your orders for the development of programs in the "Freelance" section of the Market. Also, we do not have and do not plan to have a software solution for decoding the source code back to the original form. All requests to send previously sent original source code, including persons representing their owners will be ignored. So please, do not ask us to do it.
!!!Anyone who understands the purpose of this software and who finds this useful is welcome to comment the post.